If you’re collecting information of any kind from your customers, data security is non-negotiable. More than ever, consumers are wary of handing over their personal information to businesses for fear of breaches and other security risks.
According to Secure List, 70% of the web applications contain vulnerabilities associated with access control issues. worry about the security of the data they submit through web forms. However, when these security incidents happen, businesses are liabile and subject to fines and lawsuits for not ensuring the safety of consumer data, even if the breach happens through a third-party vendor. It is still that organization’s responsibility to conduct security assessments on their supply chain as data stewards for their clients.
FormAssembly takes data security very seriously, and we want to arm you with all the information and functionality you need to keep customers’ data secure. Keep reading for a comprehensive guide to collecting data in a secure, compliant manner.
What is data security?
Data security is the practices, methods, and techniques involved in keeping data secure and safe from any misuse or unintended access. Data security needs to be considered from the moment you first touch a customer or prospect’s data through the entire span of time that you keep it. Your organization’s data security, or security posture is affected by the technology and applications you and your employees use, the administrative settings and access controls for your data management, and your organizational procedures around data storage, encryption, data purge, and more.
Data security encompasses all the methods and techniques involved in keeping data secure and safe from any misuse or unintended access.
Understanding the importance of data security
Compromised customer data can put your customers’ identities, finances and livelihood at risk in addition to causing serious reputation damage to your company. Lapses in data security may arise from ignored software patches, poor employee cybersecurity hygiene, or a number of other possible attack vectors. Regardless of the source of origin, attacks are serious and can cause irreversible damage to a business.
Web forms & data security
People submit information through web forms every day, from small, unimportant pieces of data to highly sensitive information, such as bank account numbers, health information, social security numbers, or credit card information.
When your customers submit information through forms on your website, they’re putting a large amount of trust in you to keep it secure, and it’s your duty as a reliable business to handle their data responsibly and not to leave it vulnerable to tampering or theft.
Threats to the data you collect

Improper access
The wrong people can get access to the data in the systems you use in a number of ways, from the seemingly benign—such as when a third-party contractor or employee without the right clearance sees information in a platform you use—to malicious social engineering attacks or exploitation of weak passwords. One way to keep damage to a minimum is the use of data masking. On FormAssembly’s Enterprise plan, sensitive data is masked by default and is only accessible by authorized personnel for specific amounts of time.
Data collected over insecure connections
You’ve probably seen first-hand a warning pop up on your phone if you’ve tried to submit payment information over an unsafe connection. If you were to ignore this kind of warning, your data would be at risk of being intercepted by bad actors. It’s the same if you collect your customers’ data over an insecure connection. For this reason, you always want to make sure data you’re collecting is protected by HTTPS and TLS 1.2.
Non-compliance with security and compliance regulations
There are a number of security and compliance regulations out there, and it’s important to know which ones apply to your business. Non-compliance can result in fines and loss of customer trust. In a later section we’ll go into detail about the GDPR, HIPAA, GLBA, and others.
Important aspects of secure web forms
When collecting any data through web forms, it’s important to keep these key aspects of secure data collection in mind.
Authentication
If you need to guard your forms against any unintentional access, authentication in the form of CAS, SAML, or LDAP can help you make sure only the right people can access your forms.
Encryption
Encryption protects the data submitted through forms by encrypting it so it can’t be read by people without the key. TLS (Transport Layer Security) 1.2 is the industry standard level of encryption and can give your customers peace of mind that their data, especially sensitive information, is being collected securely.
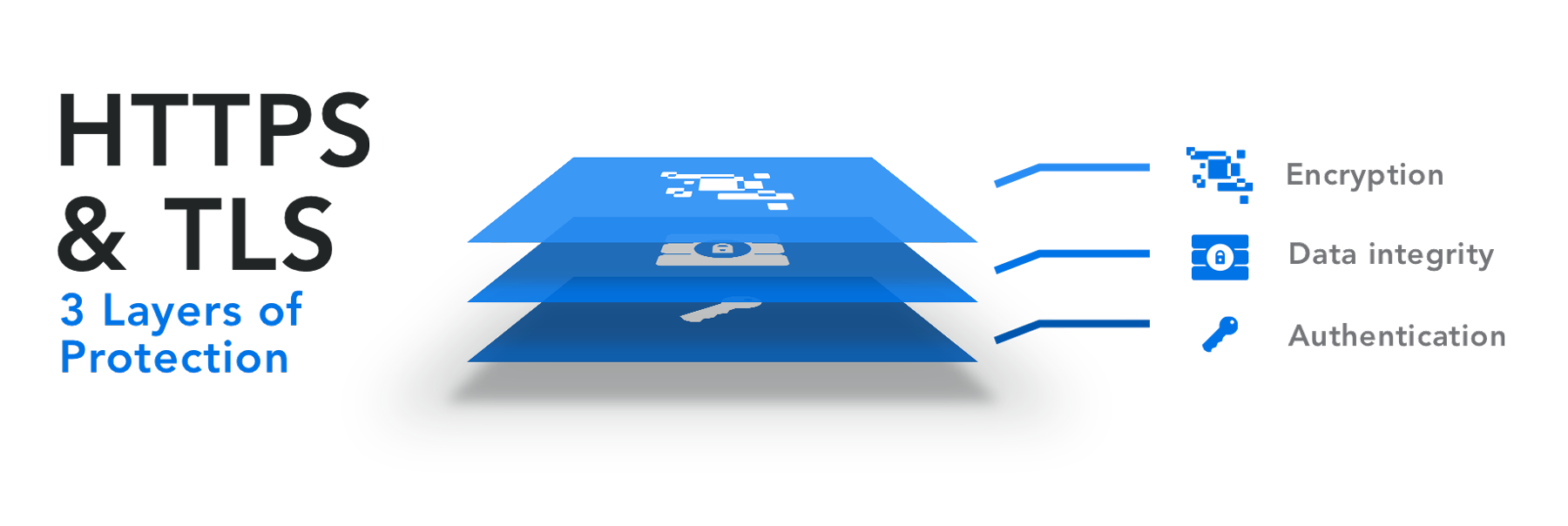
When data is sent over HTTPS is secured with the TLS protocol, three key layers of protection are provided:
Encryption—Encrypted data is kept safe from anyone with malicious intent that might want to steal information.
Data integrity—Data cannot be modified or corrupted during transfer, intentionally or otherwise, without being detected.
Authentication—Proves that your users communicate with the intended website. It protects against man-in-the-middle attacks and builds user trust, which can reverberate across your business.
If your website does not have a TLS certificate, you can direct respondents to secure web form links, such as those provided by FormAssembly.
Type of data
The type of data you’re collecting can matter as much as how you’re collecting it. Certain types of data, such as healthcare data and information gathered from EU residents, may be held to different and stricter standards. Make sure you’re considering any regulations that apply to your business.
Proper branding
Your forms should reflect the same branding as your organization so that users don’t have to wonder whether your forms are legitimate. Always use consistent, on-brand fonts, colors, and logos across your web forms. The easiest way to do this is to use a form builder that provides a customizable Theme Editor.
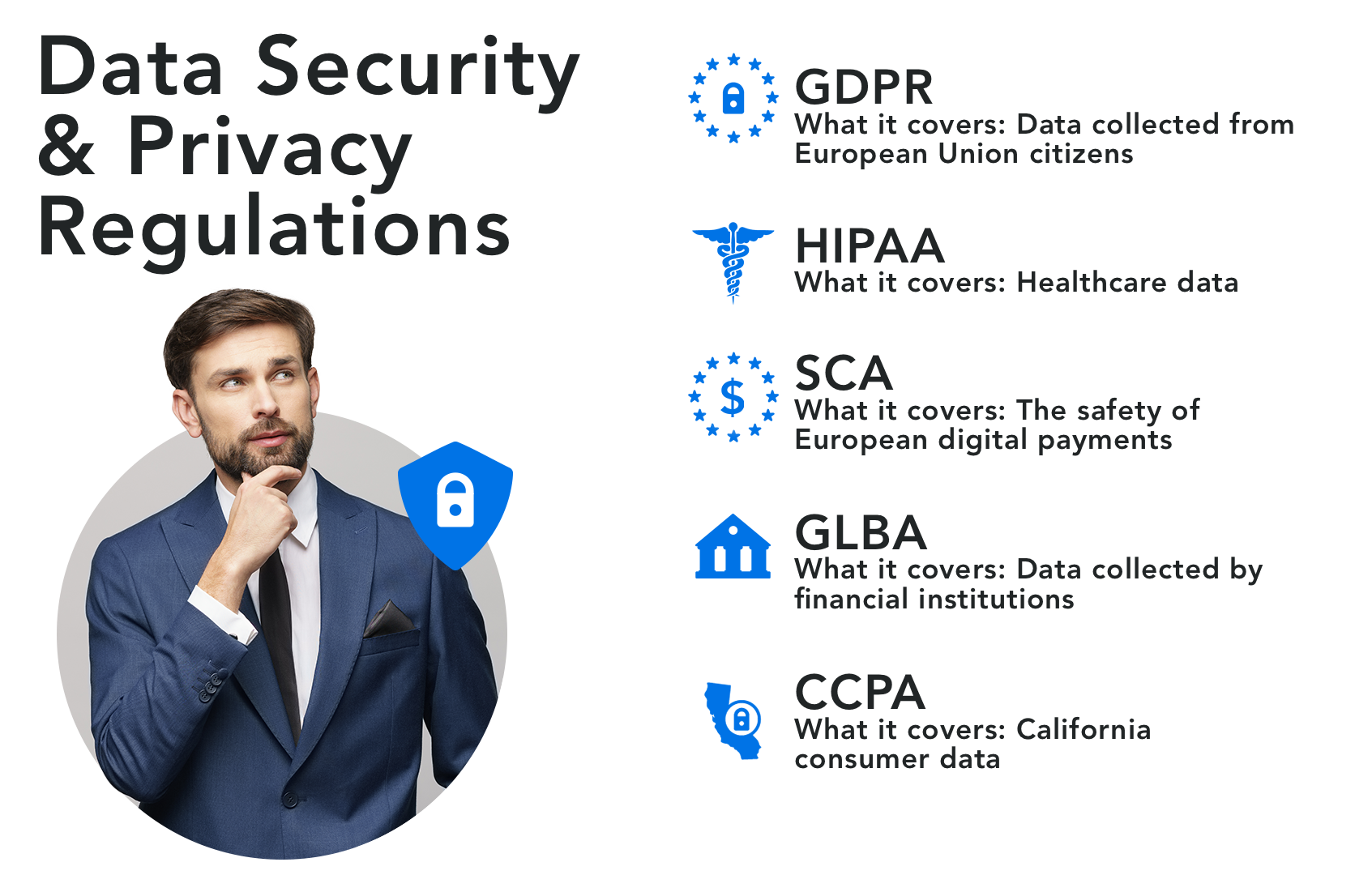
What are the different types of compliance?
The regulations that apply to you may affect the way you collect data and the tools you use. Here are some of the most common regulations that govern data privacy and security and requirements you may need to be aware of.
GDPR
The EU GDPR (General Data Protection Regulation) is a data privacy regulation that applies to the European Union. Created to safeguard data privacy for EU citizens and standardize data privacy laws in Europe, the GDPR carries large fines for non-compliance.
Among other requirements, GDPR instructs that businesses should gather consent when collecting data. It also requires businesses to add links to contact information and a privacy policy on company websites so that customers understand why their information is being collected, how it’s being used, and how to contact you with questions. Even if you’re not required to do this for the GDPR, it’s still a best practice.
HIPAA
The United States Health Insurance Portability and Accountability Act (HIPAA) is a regulation that concerns the privacy and security of PHI, or protected health information.
Under HIPAA, it’s important to use a HIPAA-compliant data collection solution to collect any PHI, which includes one or more of the following 18 items:
- Names (Full or last name and initial)
- All geographical identifiers
- Dates (other than year) directly related to an individual
- Phone Numbers
- Fax numbers
- Email addresses
- Social Security numbers
- Medical record numbers
- Health insurance beneficiary numbers
- Account numbers
- Certificate/license numbers
- Vehicle identifiers (including serial numbers and license plate numbers)
- Device identifiers and serial numbers
- Web Uniform Resource Locators (URLs)
- Internet Protocol (IP) address numbers
- Biometric identifiers, including finger, retinal and voice prints
- Full face photographic images and any comparable images
- Any other unique identifying number, characteristic, or code except the unique code assigned by the investigator to code the data
SCA
Strong Customer Authentication (SCA) is a part of Europe’s PSD2 (second Payment Services Directive) and is concerned with the safety of digital payments in Europe. It’s important to use an SCA-compliant payment connector if you need to comply with this regulation.
GLBA
The Gramm-Leach-Bliley Act (GLBA) is a regulation that requires financial organizations to clearly communicate how they protect customers’ sensitive financial data.
Some of the key requirements of the GLBA are that you:
- Provide privacy notices
- Develop a comprehensive written security plan
- Use GLBA-compliant vendors
CCPA
The California Consumer Privacy act (CCPA) is a California regulation that protects the data privacy of California consumers, by restricting what businesses can and can’t do with their personal information.
Some of the key requirements of the CCPA are that you:
- Add an opt-out option on your website and update your privacy policy
- Have a system in place for processing data requests from customers
- Implement a disaster response plan and stay educated
- Use CCPA-compliant data management tools
Now that you know more about how to create secure web forms, take the next step and upgrade to a data collection platform that supports your compliance needs. Request a free trial of FormAssembly today!



